Phishing Attacks
Do you know the methods of the attackers?



How can I protect myself and the university?
Use our checklist:
If you have to answer one or more questions with “yes”, this may be a phishing attack. But some phishing e-mails seem so real, that it only makes sense to be aware. Therefore, we advise you to be generally careful when dealing with your e-mails.
| O | Unknown/ |
| O | Is the greeting impersonal, missing, or in a different format than the rest of the text? The same applies to the tone of the e-mail or conversation. |
| O | Are the contact details or the signature incorrect? Is someone calling you from an anonymous number or from an unknown country? |
| O | Are you instructed to open attachments? |
| O | Are you instructed to open links? |
| O | Are you instructed to send gift cards or carry out a bank transfer? |
| O | Are you asked to disclose confidential information (e.g. for login data, internal contact details or requested to make a payment) |
| O | Are you asked to act quickly? Are you threatened with negative consequences? |
| O | Does the e-mail contain many typos or wrong letters (especially Umlaute)? |

Do not open phishing e-mails and delete them immediately.
You already opened a phishing e-mail? Please contact the IT Support / +49 621 181-2000 without undue delay or use our form. The sooner you contact us, the sooner we can do something about it.
More information on the checklist
Is the sender trustworthy?
- The sender name that is displayed: In Outlook, you can hover the mouse over the name of the sender. The contact details open and you can enlarge them to see the complete sender information. In Thunderbird, the sender is in angle brackets < >.
- Senders can be forged easily: The e-mail header can (but does not have) to contain technical information on the recipient and transmission (received). If you want to be sure, check the header or ask the IT support for help.
- Request a user certificate and look for certificates of incoming e-mails: With user certificates (also called digital signatures) you can sign your e-mails digitally. In addition, your e-mail program checks the signature of incoming e-mails, if they are signed (e.g. with S/
MIME). You do not have a user certificate? Here you can request a user certificate. - I received phishing e-mails from a known sender, how can this happen? If the account of an employee has been hacked, it is possible that hackers use the account to send phishing e-mails to persons inside and outside the organization.
Unfortunately, a trustworthy sender does not guarantee a trustworthy e-mail. If you are unsure, use another way of communication to ask the sender directly. You can contact employees of the university via phone or other communication tools.
How can I identify malicious attachments?
- The file ending (e.g. file.pdf) is not an indicator for a secure e-mail, since there are some tricks to disguise the file ending. In the tab view in the explorer, enable the file endings by checking the box file name extension. Now you see the complete file name, e.g. File.pdf.exe
- Be aware of empty files: Is the file preview empty? This is a common trick to make you curious.
- Protected view: All office products offer a protected view. Activate the editing mode, but no macros.
- Do you know the notification “Program XY wants access to your computer”? If you have opened an attachment that asks for access rights, deny the access and inform the IT support.
- If you have opened a file and your computer seems to be infected, please contact the IT support.
If you are unsure:
- Use another way of communication to ask the sender about the attachment.
- Check the attachment for viruses or ask the IT support for a virus scan in a secure environment.
Please check your computer for viruses at regular intervals.
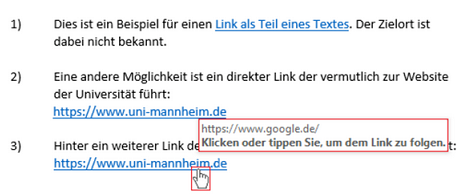
How can I identify the target of a link?
1) Hover the mouse over the link. After a short while, you will see the target link (see picture).
As an alternative, you can also turn off HTML so that you see your e-mails in text form first. Follow the Microsoft instructions: https://support.office.com/de-de/article/lesen-von-e-mail-nachrichten-im-nur-text-format-16dfe54a-fadc-4261-b2ce-19ad072ed7e3
2) Check the domain part which is the name of a website, e.g. www.bwl.uni-mannheim.de/programs.
Be aware of forged domain parts! Here are some examples:
- Fake domain name
- www.uni-mannheim.de.website-of-the-attacker.com/programs/
- Similar looking characters/
numbers - www.uni-mannheirn.de/programs
- Mimicking the actual domain name
- www.mannheim-uni.de/programs
- Typos or transposed letters
- www.uni-manhneim.de/programs
3) The e-mail contains a link to a login page? => It is better to manually open the login page of the provider, even if this takes two clicks more. Better safe than sorry.
- Fake domain name
Negative consequences? The reality check.
Ask yourself: “How plausible is the issue of the sender?”
- Would my supervisor urge me to transfer money directly and without undue delay, without referring to a business transaction?
- Would I be threatened with negative consequences by the IT support, if I deny to disclose confidential information right away? (Tip: Ask your colleagues to listen to vishing calls as well, if you are unsure)
- Would Paypal ask me for my password?

Do you want to learn more about phishing? We offer trainings at regular intervals. Please register via the continuing education program of the University of Mannheim. In our training overview, you will find more information on our trainings.
Why are phishing attacks so successful?
Thinking, fast and slow by Kahnemann
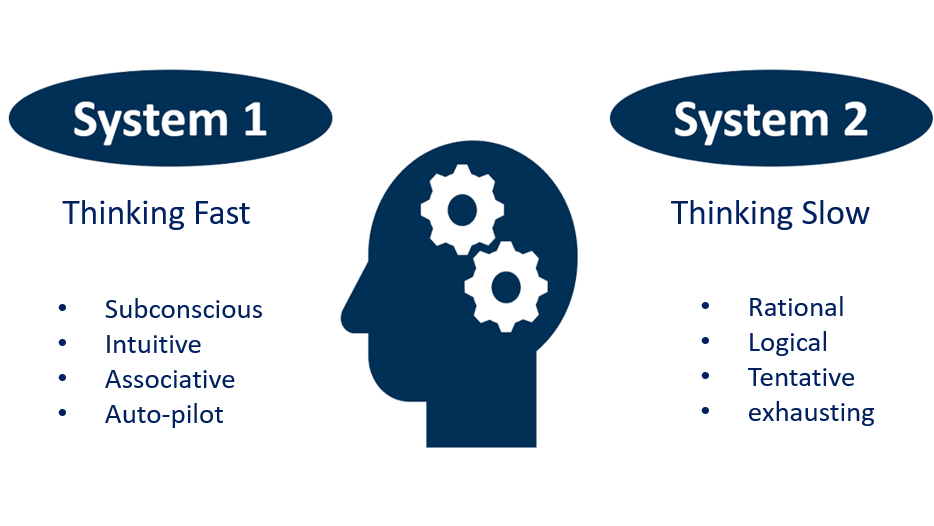
System 1 is responsible for System 2 which may lead to several problems, when a phishing mail is in your inbox, because we are used to
- automatically open and scan our e-mails
- quickly click on links since we know that the links forward us to the important information
- when opening attachments.... oh, there is an issue with the attachment => okay, then let's allow all macros
In addition, the design is familiar. Everybody knows the annoying error message. We are intuitively clicking the box, before we read and understood the message.