Why are spam e-mails dangerous?

Spam or junk mail is the term for unwanted e-mails of any kind, e.g.advertisements and scam e-mails as well as hoax (fake warnings) and phishing e-mails.
- The e-mail source code may contain malicious code that is executed when you open the e-mail.
- Be careful when you open attachments. Attachments may contain malicious software.
- Links from spam e-mails often link to fake websites. Opening the website may be sufficient for infecting your device.
- Phishing = Attackers try to steal personal data such as login data, addresses, e-mail addresses or credit card information.
Examples with pictures:
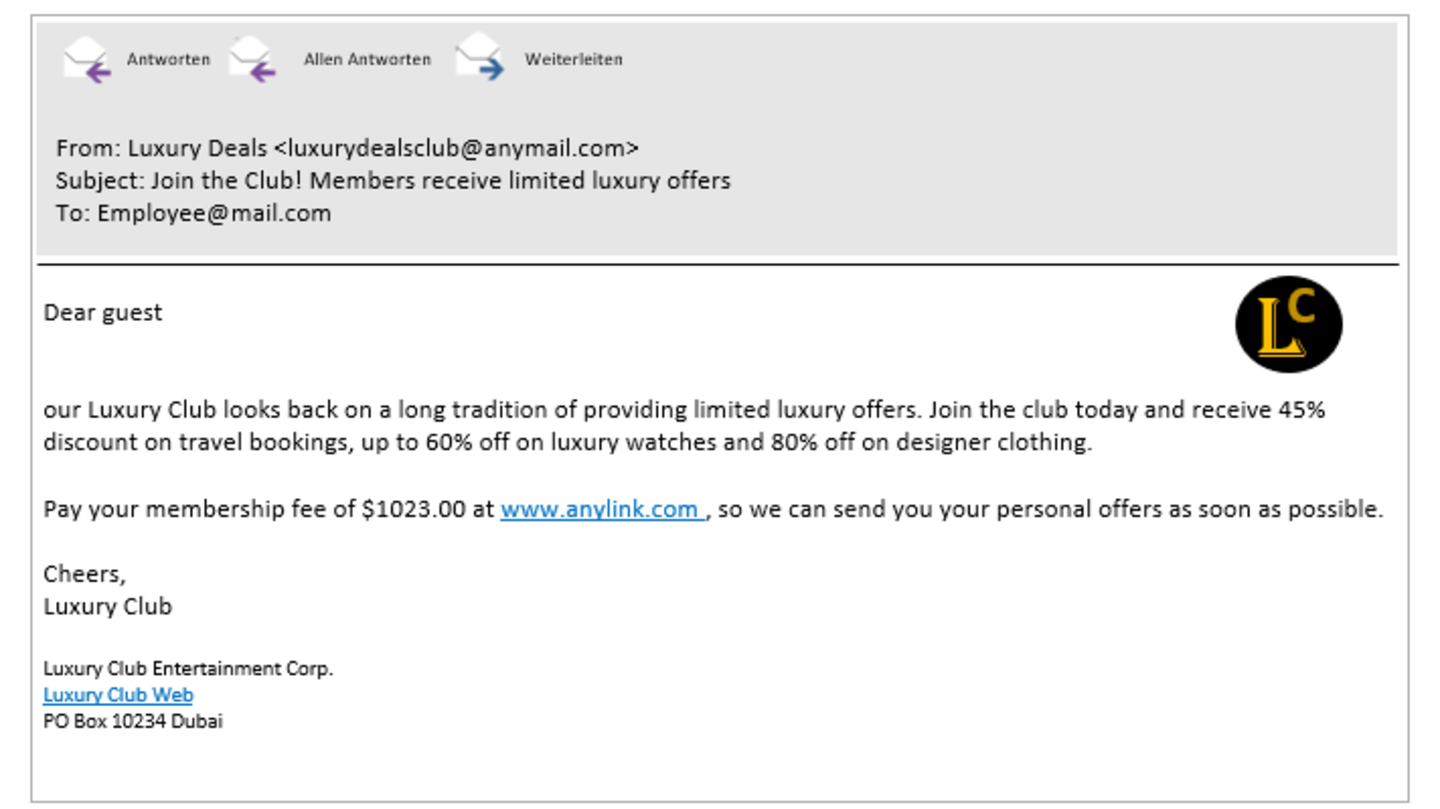
E-mail advertisement
Attackers often use the latest topics and currently, the coronavirus pandemic is one of these topics. We advise you to delete such e-mails right away. If you receive a lot of e-mail advertisements, we recommend to set up a spam filter. Here you will find instructions for setting up a spam filter.
Scam – Advance-fee fraud
Maybe you know phone scams or scam letter: You are the winner! Send us your contact details and pay 200.00 Euro upfront to secure your prize.
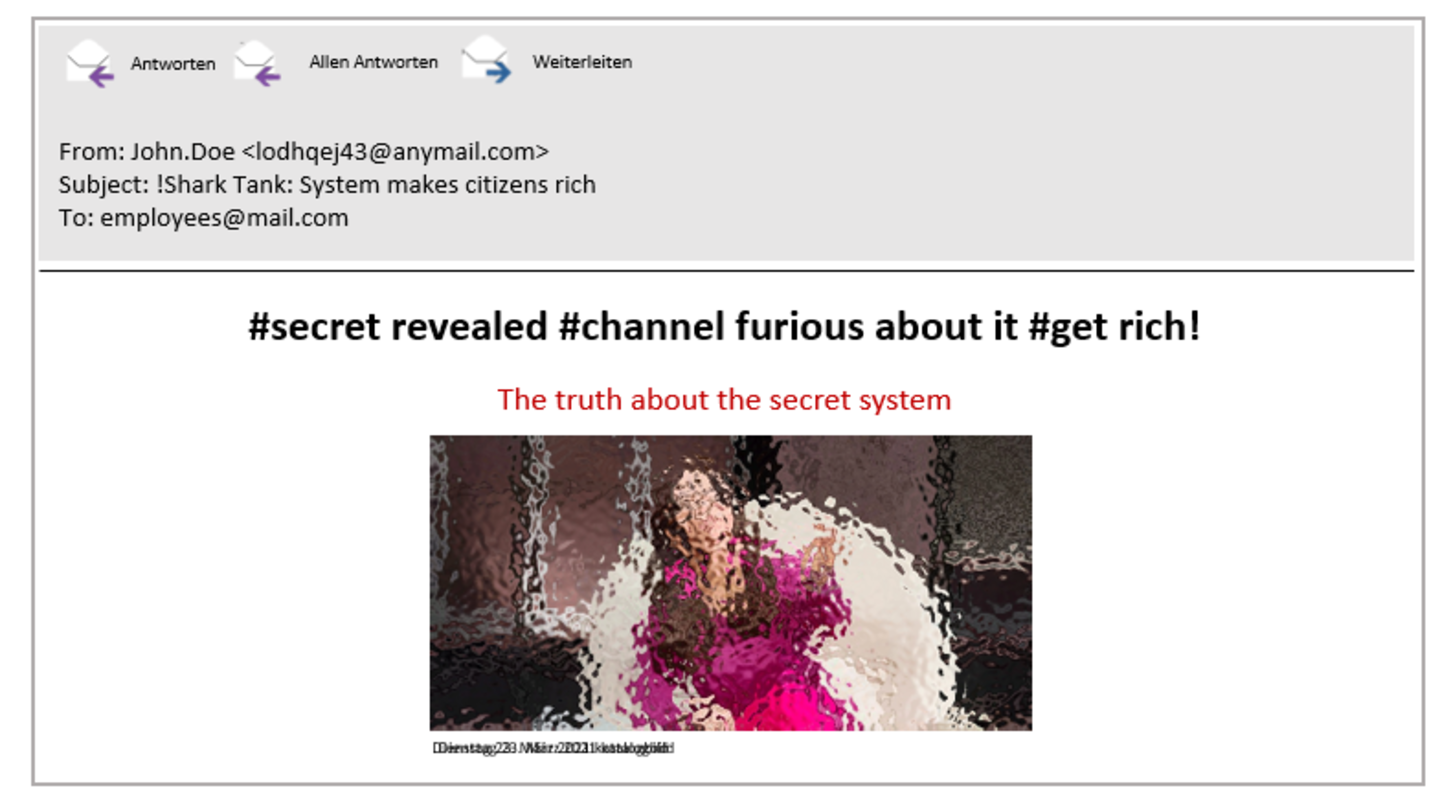
Hoax – Fake messages
Hoax (fake message sent via e-mail or messenger)
These messages are often sent in the form of chain letters and aim to motivate the reader to share the fake message. Some examples might be: “Tomorrow, a space tax will be introduced. It will become expensive for the inhabitants of the earth.” (Note: The tax is completely ficticious).
The recipients of fake messages might feel insecure, frightened or like they are missing out. The “Höhle-der-Löwen” spam also uses the fear of missing out. The scam suggests that people who do not become active and read the e-mail have to blame themselves if they do not become rich.
Phishing for login data
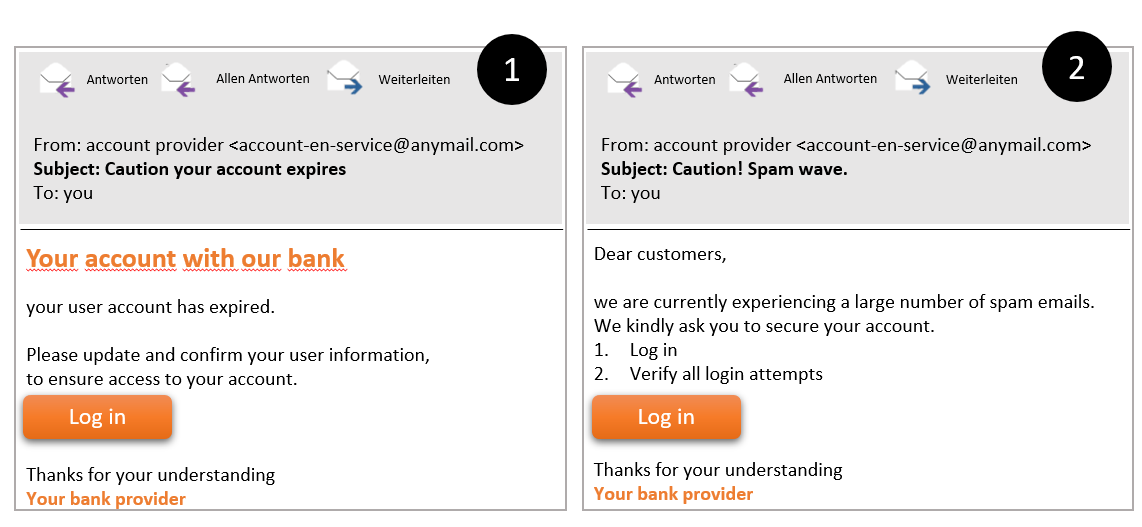
Do you know phishing e-mails, in which someone asks you on a pretext to disclose your user data (e.g. your account will expire, secure the access to your account (see the first example)).
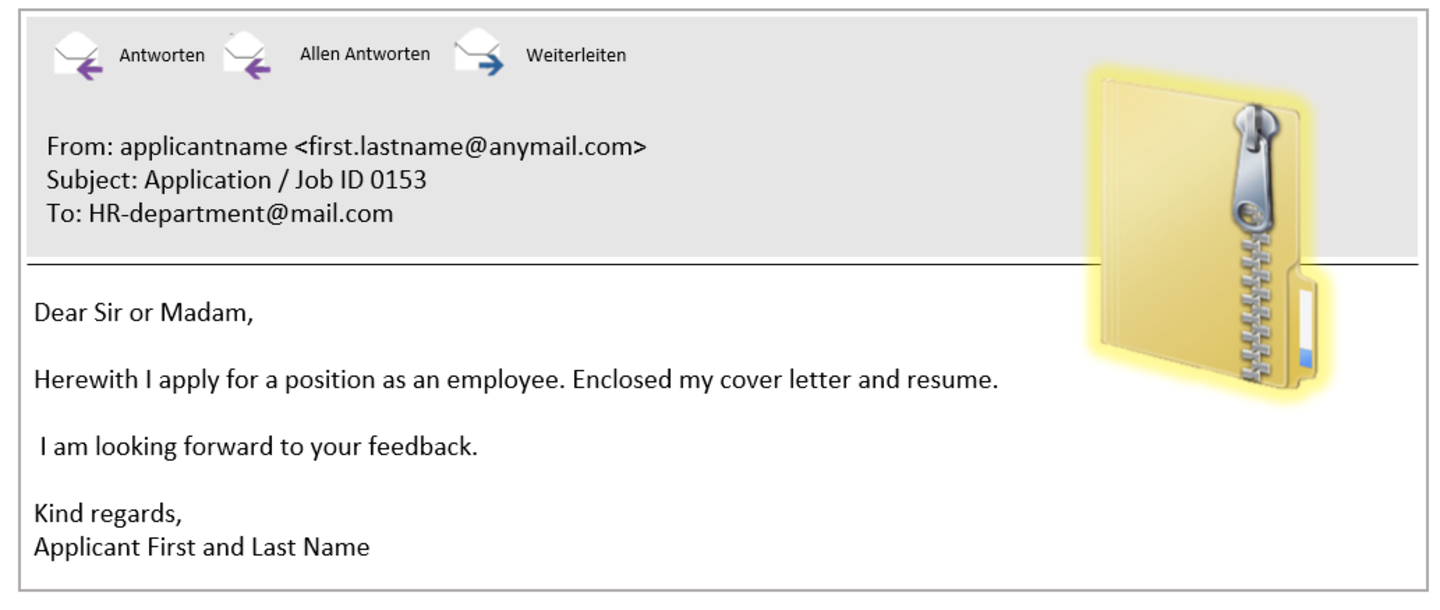
But do you know the latest trick? Currently, attackers warn of attackers, meaning themseelves (see the second example). Really clever!
Applications are special cases
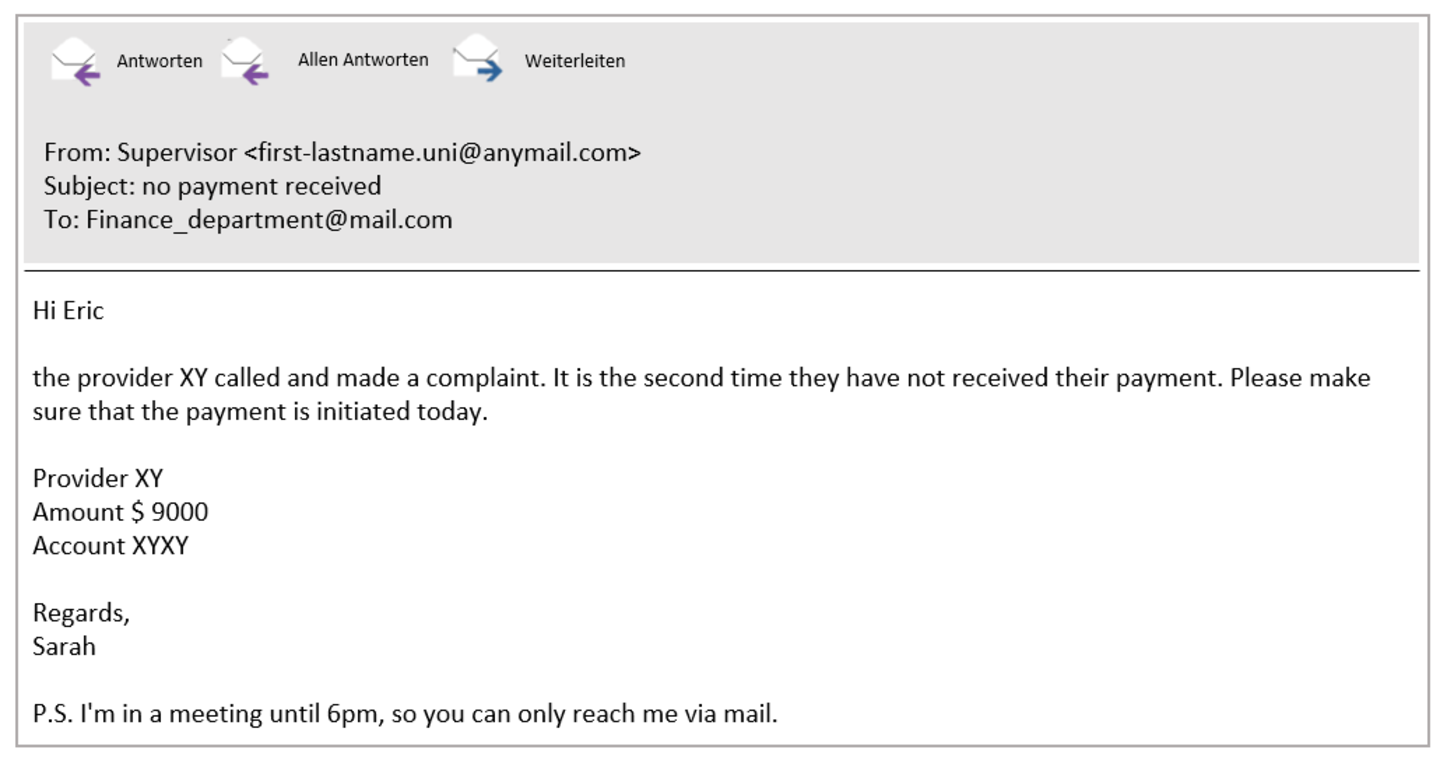
Did you see the example where someone sends an application via e-mail? Does this e-mail seem suspicious?
This is the nasty thing about spam e-mails. Applications all look alike at first glance. If you receive an application, you have to open the application to have a look at it.
We have created a quick check for applications.
- If you receive applications, always check the attachments for malicious software.
You should become suspicious, if
- you are asked to open the application by clicking on a link,
- the attached file is encrypted,
- an executable file has been attached (e.g. a macro or .exe).
You are unsure? Ask the information security team or the IT support team.
CEO fraud: Attackers claim to be your supervisor
- Scammers collect every information they can about the university. They use published reports, websites, information from the press and social networks. Sometimes they even attack the technical infrastructure to listen to conversations and to engage in the conversation.
- If the scammers have sufficient information for their scheme, they contact the employees they observed and claim to be their managers, CEOs or business partners. Usually, their victims are employees from the bookkeeping or accounting department. The scammers request the employees to make an urgent transaction.
Overview on possible attacks
Spoofing: Attackers create fake websites
Not only links from malicious e-mails but also search results from a search machine can link to dangerous websites.
There are two types of websites:
- fake websites: the attackers imitate existing websites to steal customer information, e.g. login of a bank website, Amazon start page, etc.
- Enter the address in your browser and make sure that the address is without typos.
- self-operated websites: the attackers have their own website, e.g. a fake web shop. When you buy a product, you enter your data. You will never receive the product and the attacker has your credit card details.
- Do not buy anything from shady web shops (no matter how good the offer seems). Check user ratings on other portals, e.g. on yelp, google, tripadvisor, etc.
- Do not let certificates guide you, these certificates may also be fake.
- Go to www.verbraucherschutz.com/warnungsticker/ and check if the shop is listed in the warning list of the consumer protection agency (Verbraucherschutzzentrale) in Germany
- fake websites: the attackers imitate existing websites to steal customer information, e.g. login of a bank website, Amazon start page, etc.
Unknown caller or forged SMS
Vishing (phishing via phone)
- Someone calls you and presses you for information about your company.
- Someone calls you and claims to be a supervisor. He requests that you make a transaction for work that the caller allegedly conducted. You are pressurized or insulted.
- Some grandchild tricks, e.g. a caller claims to be a grandchild in financial need, also belong to the vishing category.
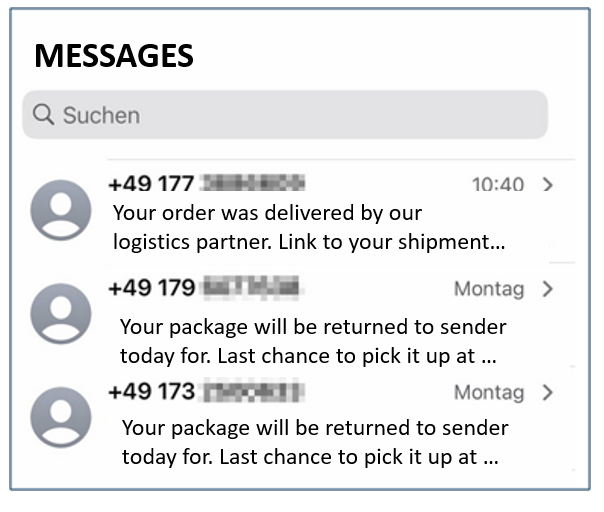
Smishing (phishing via SMS)
- Link via SMS, e.g. your mobile phone plan is too expensive, have a look at our new offer online.
- or a SMS with a request to pick up a (non-existent) package, including a link to check the delivery status.
What are the dangers of social networks?
- Sending private messages can be used to steal information.
- Media files on popular platforms play an important role when it comes to distributing spam. They motivate users to click on malicious links that are behind videos, alleged quiz applications or fake ads, mostly displayed as shortend URL (shorter URL).
=> Check the URL and/
or the links => Be careful when publishing private information when you use social networks or job networks for work or private purposes.